STHACK 2024
This years Sthack CTF took place the 24th of May. You can find a description of this event here.
For the last three years, the Non-Profit Hack4Values has been working with the Sthack to offer a private bug bounty program to help NGOs strengthen their digital security. The bug bounty program starts one week before the CTF, and ends around 11pm, during the competition.
I spent the first few hours of the CTF finishing my report for the bug bounty, and found a critical vulnerability! As the vulnerability is still being fixed, i cannot publish any details, however the i reported it as a Broken Access Control, with a final CVSS score of 9.1.
As this was my first bug bounty report, i was super pleased with such a high score, as i was one of only 3 teams to find a critical vulnerability. This placed my team in 3rd place for the bug bounty part of the CTF.
I spent the rest of the CTF working on the Ulysse chall, which unfortunately i did not manage to finish, however here is the writeup of the first part:
After arriving on the website and creating an account, we end up on this home page: 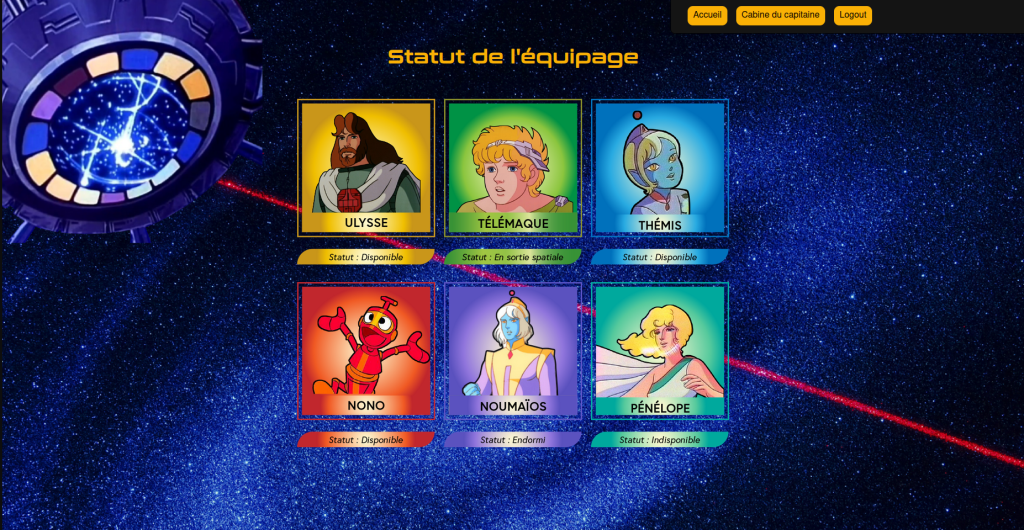
We can see that there is a captains page, however we are not allowed to access it.
Lets have a look at our cookies to see if anything is badly configured:
eyJhbGciOiJSUzI1NiIsInR5cCI6IkpXVCJ9.eyJpZCI6ImFjNTE4YTY0LWNhYzctNDQ3OS1iNmE3LTFiMDZlOGQxODkyNyIsInJvbGUiOiJjcmV3IiwiaWF0IjoxNzE2NTkxNTUyLCJleHAiOjE3MTY1OTUxNTJ9.j3KayWnbKR2sOs4PxqrhwjmZ8K19AXfETPIiSlEXT8SmaU1xARVNRSwgL9524QNV0sm1440gYLgTnRVTXNSlaQQyGaOH9rQCVVwf-YSoEwrYL0uEeSJB6MRG-f3ma8Ful8C_0tw-tVi1kQMVSK7tS4bQCY7qXXtIuqs6EZSkBqqb-SVRyMOFZVVBVGoCWumiyXtglFmYtoo-7rJtUiXJ8DTLtWwq3zEnEpBQXNFFIadJTNfXVHKLYDjcF1OeBbuhjR6HKSIsTciDiZrvvN9EPNVDfaKd4Qb2dDytFQxAQltx0ARNPW7DBlFjN-1h7RTkdLPLrnSMNnUk5kc00LLRRg
Which decoded looks like this:
{
"alg": "RS256",
"typ": "JWT"
}
{
"id": "ac518a64-cac7-4479-b6a7-1b06e8d18927",
"role": "crew",
"iat": 1716591552,
"exp": 1716595152
}
RSASHA256(
base64UrlEncode(header) + "." +
base64UrlEncode(payload),
Public Key,
Private Key
)
We can see that the payload contains a role, so our aim will be to change it from crew to captain.
By using this tool here: https://github.com/FlorianPicca/JWT-Key-Recovery, it will allow us to recover the public key that was used to sign the token. We must create a second account as the tool needs two different JWT tokens to find the public key
-----BEGIN PUBLIC KEY-----
MIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAskgpIG/4tRRHJ5qGQenQ
vXjheA0TC0uShN6PMktj6kmXgy3uKQ2eB2ODi8dQhTRZpCJ9wkpm0KeiZzpsuuGs
U4s4psT5hoScSa1s6x+Cqu9mOMn3L3FXqJZfapXcL2URE9T6PXS8mcNyrYm2a4KR
XmkLsWl2rtBkYDSItG2S7pm0V6+g2JmkTcgedhQI4lo1GIRbUMAcN+HNK71Ign3b
bGxxp+kuUWMmSpMxSFvsU61G2t2rq015WWKg7acgBfBqq9qnT7UzDGhHH+xtfoOG
m8Bz1M1ndiksmiqBLwasc85Vbf1mTpTCp+LObOawu4Gskf3jp3qU4ZM/gtEvNT0b
YwIDAQAB
-----END PUBLIC KEY-----
Once the public key acquired, we could sign a new token using a vulnerable nodejs library (jsonwebtoken) with the HS256 algorithm. Once we had signed the token with the captain role, there was an influxdb injection using nosql. I spent the last few hours of the competition following this guide, however unfortunately i was not able to get it to work.
The vulnerability I exploited involves an algorithm confusion attack. The application expects the token to be signed with RS256, which uses asymmetric keys (public/private), but accepts tokens signed with HS256, which uses a symmetric key (shared secret). By recovering the public key, you were able to use it as an HMAC key to sign the token with HS256, which should not have been allowed. I will be writing a full guide on this vulnerability soon.